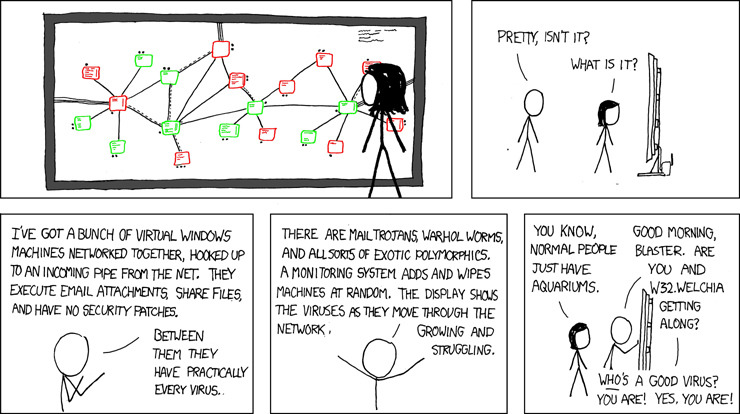
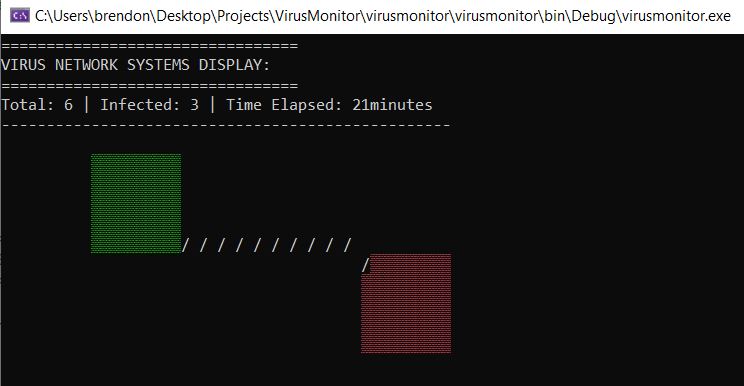
 Virus monitoring dashboard
Virus monitoring dashboard
System notificaiton of the beginning phase of infection is done by directly patching into the Windows function call to mem_Copy.
void *memcpy(
void *dest,
const void *src,
size_t count
);
Network XKCD Comic Link
* * *
#_ the asd coin cipher
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
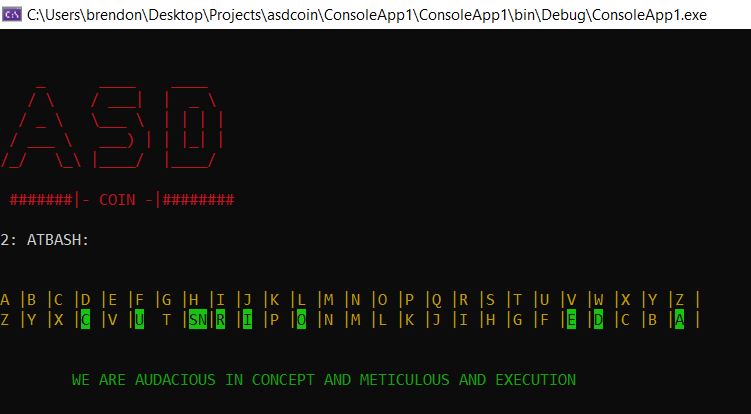 Cipher Solver
Cipher Solver
75th Anniversary Commemorative Coin Challenge Link
* * *
#_ making a tv station
...What are you doing?
...I'm taking over a TV network.
Introduction
-------------------
Traditionally broadcast television will modulate electromagnetic energy into Radio Frequencies. This is considered analog and continious, unlike digital network streaming (eg: HDMI),
that is sampled, descreate. The signal carried by the coaxial cable (PAL) is analough.
Bandwidth (in Hz)
Amplitude, frequency, and phase
Signal-to-noise ratio (SNR)
Wave seperation
|---- Raspberry Pi ---|---Station Software---|------>-----|---RF Modulation Unit---|---->----|---TV ANT---|
- RF Energy
- signal partabola focual point
- residance /very powerful - see bridge.
|\ /|
| \ / |
---------
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
Ultimate Homelab Cable Setup Link
* * *
#_ cracking crypto1
Introduction
-------------------
Histroy has been pretty clear. Never roll your own Crypto. Secure cryptographic protocols are best as open standards and will need to. 48 bit keyspace (k).
mifare Classic is old and vulnerable using a propiatary encryption protocol. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
* * *
#_ wireless proximity cards
Introduction
-------------------
Wireless proximity cards are avaiable in many different types and use cases. The diffent types generally fall into 3 categaories. 1. Access Control. 2. Signal Control. Identification.
- Magnetic Stripe
- Prox Cards
- RFID
- NFC / mifare

mifare Classic is old and vulnerable using a propiatary encryption protocol. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
* * *
#_ facebook root certificates
Introduction
-------------------
Consistent security controls and high reliability are common expectations for any systems administrator. How do you deliver both on a network with thousands of servers supporting thousands of engineers? Most off-the-shelf solutions require a compromise in at least one of these areas — and we refused to accept this.
- PKI
- transitive trust
- symet \ asym encryption
- encryption attributes\properties
mifare Classic is old and vulnerable using a propiatary encryption protocol. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
Scalable and secure access with SSH Link
* * *
#_ tapping a tel exchange
Introduction
-------------------
The SIP and RPT protocols are common in enterprise environments and often contain sesitive information. If correct security controls are not implemeted correctly SIP endpoints become a target of thread actors.
* Voip SIP strcuture and call handling proceedures.
* Handling authentication and joining a call.
* RTP carry.
Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
Links
---------
* * *
#_ my vim config
...Linux is awesome and so are you!
Introduction
-------------------
A light vim config that has been configured towards reading code and config files. I have a preference for managing a single windows in VIM with splits and using tmux for multi-window work
* light touch vim config. Ready to add file explorer, fuzzy finder and LSP as needed with plugin-manager of choice.
* relative line numbers for easy navigation. Underline and highlight of current line for clarity. File status bar. Code LF indicator at 100 characters.
* you can find a copy of the .vimrc configuration file here
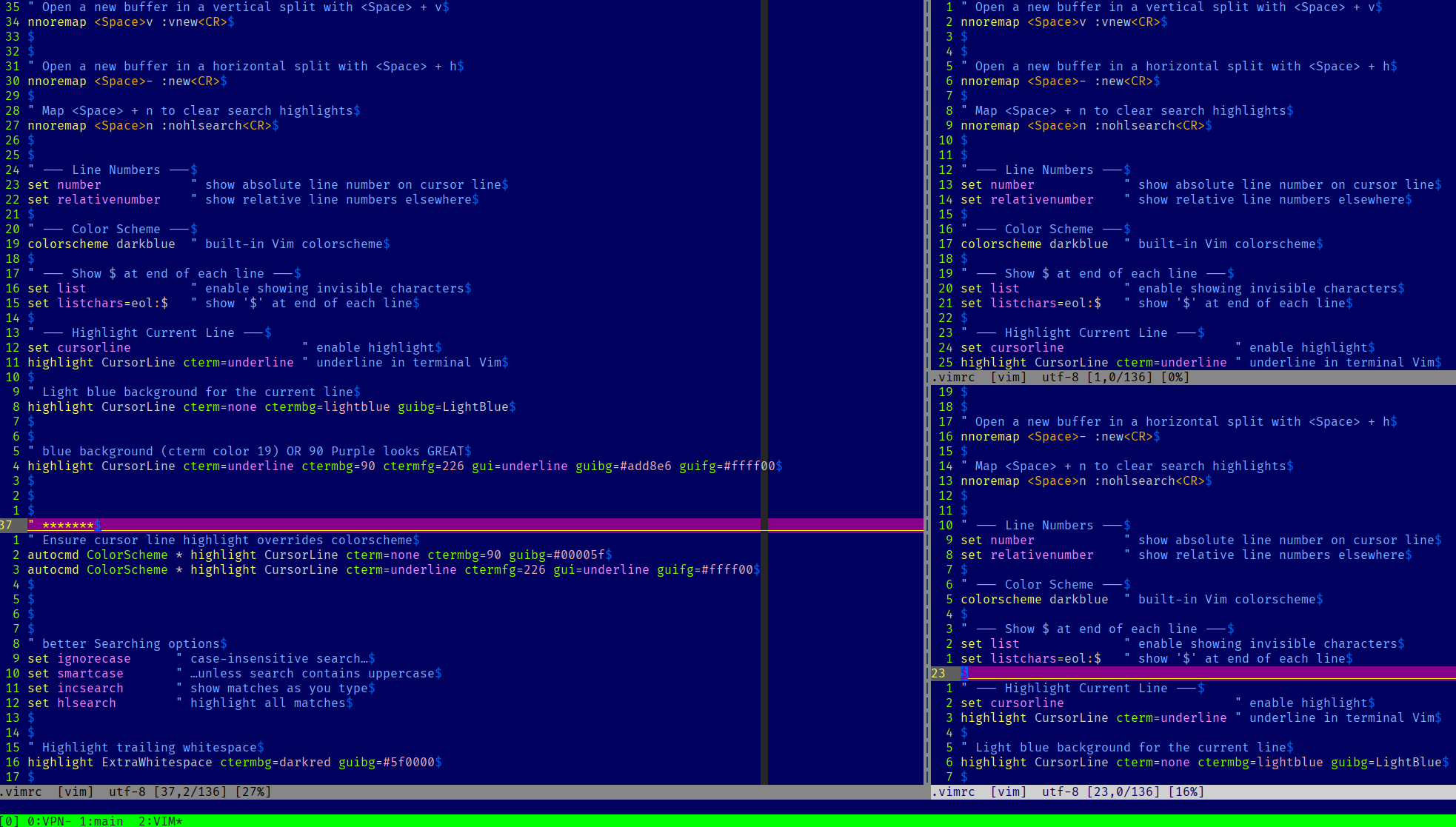
0 to LSP : Neovim RC From Scratch Link
* * *
#_ outside domain enumeration
Introduction
-------------------
Two common techniques for external domain enumeration are often mentioned but rarely explained in depth:
(1) LDAP anonymous binds (2) SMB/RPC1 null sessions.
Although both allow enumeration, they operate over different protocols and expose different classes of information and often discussed interchangeably.
* attack opportunties open up when account information can be enumerated.
* common attack from outside the domain perimeter is - connecting to hiden services through null authentication.
* These two attack methods are commonly conflated but use two different communication protocols.
This is a well worn attack path and is commonly seen in CTFs and introductory offensive security cources.
SMB not only provides file shares but is the transport for multiple backend services. You can get a shell, change the properties of services and enumerate/process security policy all through SMB.
The Inter-process Communication share \\IPC$ is the gateway to special operations using named pipes. In this case authentication happens through SMB. Once authenticted by credentials or ananoymous access
through a null session. This typically occurs because a domain has been updated from a old operating system version and the security policy has not been updated by the system administrator1.
Operations through SAMR2 are based on objects and access is handled through the provision of object handles that are provided to the client as an access token.
Once authenticted:
- a Connect Handle is provisioned and provided to the client.
1. Server Message Block/Remote proceedure Call
2. Security Account Manager Remote Protocol
SMB and Null Sessions: Why Your Pen Test is Probably Wrong Link
Security Account Manager SAM RPC Link
* * *
#_ type juggling
Binary-Safe is the watchword
Introduction
-------------------
When comparison operations are executed at the binary/byte/hex level - they are strict and only one path leads to a pass. This can be very restrictive and does not work for all situations of user input from general purpose computing that you might want accomodated.
Lose commparisons can assist in this situation, that will allow multiple paths to a pass for a single input (Type Coercion)/Casting.
* Data types are critical in computer operations, everything from pointer arithmetic, to CPU instruction selection for int(ALU) or float(FPU) operations, to the evaluation of high-level language abstractions.
* With PHP loose comparison - multiple paths exist to the accept path. 'secret' === 'secret' = (is equal). 'secret' == true = (is equal).
* This behaviour can be helpful but really dangerious in particular situations, like with authentication.
The common approach for authentication is:
+--- take user password as text to server. ---+ +--- transform password with known algorithm + salt. ---+ +--- retrive password representation from database. ---+ +--- comparison ---+
- We have some comparisons going on. Looks strict and safe, moving right along >>
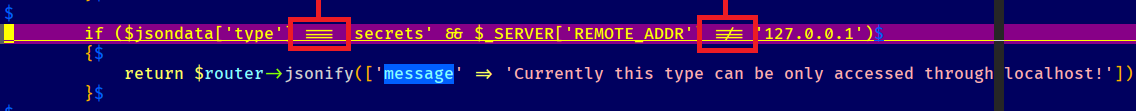
- We have some branching logic through a SWITCH statment. Although the PHP (equals) == === are not present a evaluation/comparison and branch are happening!

- Coding my own lab in PHP - we can see strict comparison case is applied to the String literal "secrests" with access denied. Access granted with Boolean true of type Boolean (true == 'secrets').
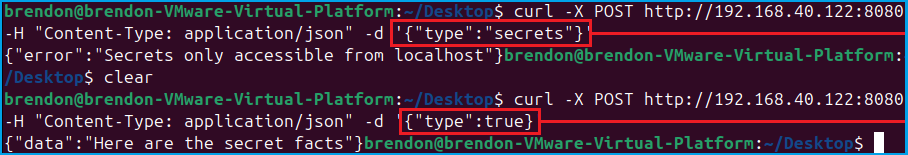
Solutions:
- Comparisons for authentication material (usernames, passwords, hashes) should ALWAYS be Binary-Safe.
- Ensure value lookups are in Constant time. (hmac.compare_digest[Python], hash_equals[PHP], crypto.timingSafeEqual[Node], bcrypt, argon2)
TL;DR
In PHP using == can cause strings that look like numbers to be coerced into numeric form.
This allows authentication bypasses if stored hashes can be shaped into “0e…” patterns that evaluate to 0.
var_dump("0e12345" == "0"); // true
var_dump("0e98765" == "0e12345"); // true
PHP Type Juggling - Why === is Important - Bug Bounty Tips Link
* * *