#_ web security
A running rough guide and notes into web security. Thoughts are my own.
serialization of objects
* data of an application sometimes need to be encoded as bytes, stored on disk or sent across the network. In Python you can use 'pickle' or 'BinaryFormatter' in .NET.
* These bytes can be received by the backend server so business logic processing can use/store or re-tranmitt the data within the byte stream.
* The bytes are typically unpacked into an object, filtered and proccessed as needed by the application.
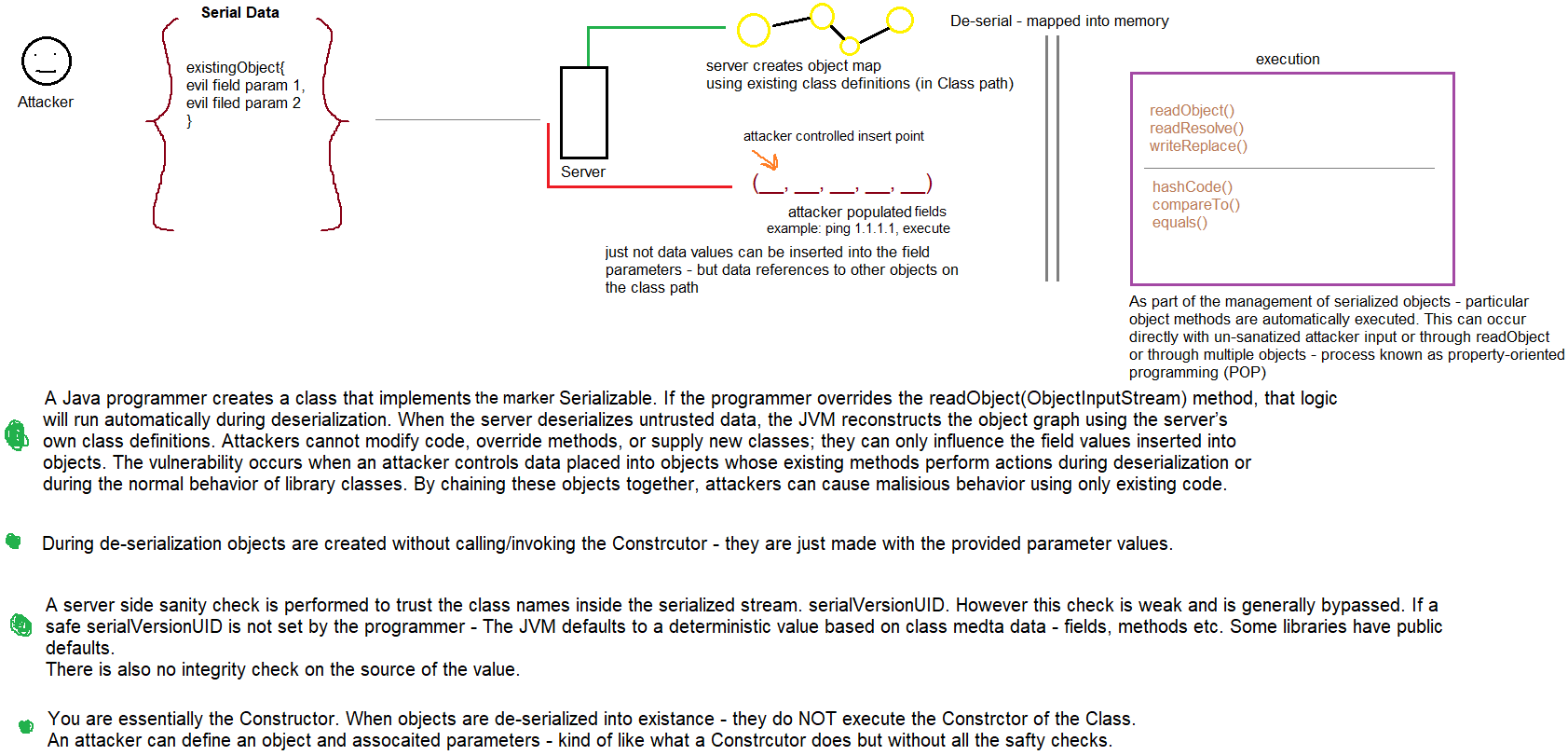
* any user supplied data should be {inspected, sanatized, strictly encoded as content not code}. If security is not applied correctly, an attacker can embed
a chain of functions and parameter values that the server will received and execute directly.
Docker ASP .Net core application that receives unsafe user input from a front end web application.
The input is accepted, serialized into a object within the application memory space.
* * *
OMG how dangerous is XSS
* Although Javascript is a client-side language executing within the browser sandbox, a few security misconfigurations can potentially compromise the entire network. * A high privledged user connecting to an internal web resource - thinking they are safe becuase there are no external routes to that internal ldap web app - that xss is all about website defacement and alert() is take a significant risk. * 3 security concerns. Session Hi-Jacking, Cross-site-Request-Forgery and enumeration. * It was a typical occurence when on engagments that the client had little or no network segmentation in place, and it was often received as a low priority task. I have been able to access router, Vsphere, SAN storage soultions, CCTV interfaces from low and public company networks and typically running old software versions.

* * *
javascript prototypes
* The root object (parent) that all sub-objects (chridren) inherit from is 'Object.prototype'. Constructor function is 'Object'. Objects created with Object.create(null)
do not inherit from Object.prototype - Good secutiy hardening practice.
* As part of the default Constrcutor the accessor '__proto__' contains a property that is a reference/pointer to the current Objects prototype.
* Functions can be attached to variables – essentially creating the functionality of a Class.
* Ability to write properties to a up the tree (root/parent level) and Deep Merge them across multiple chridren objects is a flexability and feature but if handled
incorrectly leads to vulnerabilties.
* for exmaple: an object attribute is key\value that is evaluated for access to a restrcited function or section of data. In this example the key\value pair {admin:true}.
